Governance
Information Security and Protection of Personal Information
Ryohin Keikaku recognizes that information security risks are an important management issue, and hereby establishes an Information Security1 Policy to properly protect information and safely manage information assets.
1. Definition of information security
"Information security" refers to the protection of information assets handled by Ryohin Keikaku from threats related to confidentiality, integrity, and availability, and includes cybersecurity. Cybersecurity refers to taking measures necessary for the safe management of relevant information, such as prevention of information leakage, loss or damage, and measures to ensure the safety and reliability of information systems and information communication networks in order to properly maintain and manage their condition.
Purpose
Ryohin Keikaku created the Information Security Policy with the aim of upholding the trust of its customers and society. We take basic and advanced measures to safeguard the information assets that have been entrusted to us by customers and related parties, as well as to comply with relevant laws and regulations and enhance our global corporate brand.
We are committed to strengthening information security by adhering to our Information Security Policy and Privacy Policy,2 protecting information assets against potential threats, and managing them in a proper manner.
2."Privacy Policy" is defined separately in accordance with the Personal Information Protection Management System (PMS).
Basic Approach
1.Establishment of an information security management system
Ryohin Keikaku will continuously improve its information security through the establishment of an information security management system. This system involves identifying information assets, analyzing the risks associated with each asset, and taking appropriate actions to implement countermeasures against unauthorized access, viruses, and leaks.
2.Protection of information assets
Ryohin Keikaku takes appropriate organizational and technical measures to reliably protect the confidentiality, integrity and availability of information assets.
3.Compliance with laws, regulations and other rules
Ryohin Keikaku complies with laws, regulations and other rules regarding information security and protection of personal information.
4.Implementation of education and training
Ryohin Keikaku provides essential education and training to ensure that all executives and employees fully recognize the gravity of information assets.
Scope of Application
All companies and bases of the Ryohin Keikaku Group
All executives and employees of the Ryohin Keikaku Group
All information assets used and owned by the Ryohin Keikaku Group
Management System
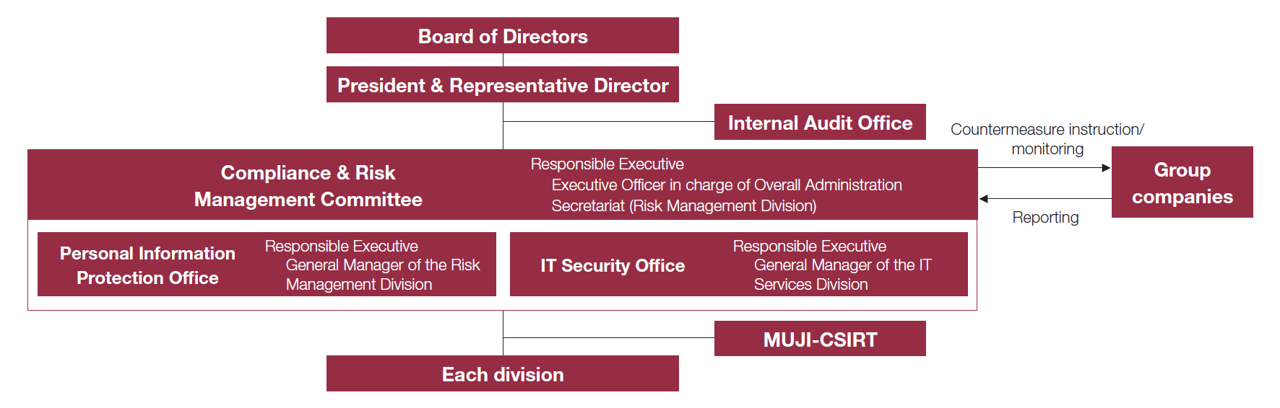
At Ryohin Keikaku, the Compliance and Risk Management Committee, which is chaired by the Senior Executive Officer, oversees relevant activities of the entire Group based on its basic policies. The committee has established the IT Security Office and Personal Information Protection Office to accurately grasp the status of information security and to discuss and promote countermeasures. Each Group company and division appoints a person in charge of information security and strives to strengthen and thoroughly implement the information management system throughout the Group.
The Personal Information Protection Office formulates rules and policies for personal information management and manages the overall process. The IT Security Office builds, maintains and operates the IT infrastructure environment in compliance with regulations and policies, and works for its continuous improvement.Reports on the activities are made to the Compliance and Risk Management Committee, which meets four times a year, and the details of deliberations are reported to the Board of Directors at least twice a year.
Information Security Management System
Protection of Personal Information
Ryohin Keikaku conducts personal information protection activities based on its Privacy Policy for personal information handled in all business activities and adopts necessary protections and appropriate security measures.
We appoint a person from within the organization with the ability to understand and implement personal information protection as a "personal information protection manager." This person assumes responsibility and authority for implementing and operating the personal information protection management system.
Measures to Raise the Level of Information Security
In FY2023/8, we worked on creating systems compliant with the Information Security Management System (ISMS) and inaugurated the Information Security Incident Response Team (MUJI-CSIRT). The goal of these measures is to establish a risk management system mainly for the information security of the Ryohin Keikaku Group as a whole. To minimize risks, MUJI-CSIRT is charged with responding to and resolving cybersecurity incidents, making security improvements and by conducting other related operations. Members responsible for promoting initiatives are selected by each department to ensure a rapid and efficient response across all departments. We formally joined the Nippon CSIRT Association in August 2023.
Training on Information Security
Ryohin Keikaku recognizes that the thorough comprehension and participation of all employees is essential for information security management. Based on this understanding, we provide information security training to all executives and employees. We also regularly conduct the following initiatives, which are effective for continuously improving security literacy, assessing the level of understanding, and raising awareness. By fostering the literacy for security throughout our organization, we aim to become a company that is resilient to cyber risks.
1.Conduct an e-learning course on information security for all employees at least twice a year
2.Conduct training on targeted e-mail attacks for all employees twice a year
3.Provide appropriate reminders prior to long vacations and other events, and conduct awareness-raising activities and follow-ups during daily work
Information Security e-Learning
| Implemented | Training Theme | Participation Rate | Number of Participants |
|---|---|---|---|
| December 2022 | Infromation security | 80.5% | 1,528 |
| March 2023 | Personal information protection | 77.5% | 1,858 |
| September 2023 | Social media and stealth marketing | 87.0% | 2,076 |
| February 2024 | Personal information protection | 41.9%* | 4,472 |
*Starting from the training session in February 2024, the scope of participants has been expanded to include all employees, including partner employees and part-time workers.
Moving forward, we will further strengthen information security education for partner employees and part-time workers.
